Does Tor protect your privacy like a VPN service while you address the dark/deep web? Yes, Tor (The Onion Routing) strengthens your privacy and is a much safer option than other services for browsing the Dark Web.
To understand clearly, one must know about the three levels of the Internet: The Surface, Deep, and Dark Web. The Dark Web is a sub-section of the Deep Web and can only be accessed with special software. It is a collective of hidden sites.
Tor is a much safer option than any other service. Tor is a network of thousands of servers or nodes which volunteers run. When you access any website through Tor, it completely replaces your actual IP Address. It also encrypts the data being sent from your device to keep internet traffic hidden.
However, Government agencies, your Internet Service Provider, and other third parties might be able to detect that you are using Tor. Because of Tor’s illegal and forbidden activities, its bad reputation can grab unwanted attention from third parties, which might actively block you from using Tor.
TOR plans a VPN-like Service to address the deep/dark web to enhance your privacy and security while exploring the Dark Web.
How to Use TOR for Browsing Dark Web
Tor provides the tightest production and high security and blocks data tracking. It hides all the internet activities even from Internet Service Provider. Circuit relies on multi-layered encryption, so you must connect to three relays before opening your destination address. And because this connection slows it down more than the other browsers.
You can also check our beginner’s guide to Navigating the Dark Web Network
- To download Tor, go to www.torproject.org in your regular web browser (e.g., Chrome, Firefox) and search for “Tor Browser.”
- Click on download by choosing the appropriate version for your device (macOS, windows, etc).
- Search the file in downloads and run the installer.
- Now follow the prompts, and choose the installation location.
- Open the browser and do some security settings because you will access the market.
- Now go to advanced security.
- Select the Safer option for security.
- You can block dangerous content and download them automatically from the bottom.
- Close the tab and re-open it to see if you are browsing on the Safer option.
- Now clear your history to get a new, clear page again.
- Then, connect your Tor browser.
- Now search any dark websites or hidden links.
- Updated onion links will be shown; choose the sites you want to visit.
- You can offer your network to the Tor circuit as a Tor relay or bridge if you are an expert.
- More relay exists means the speed of the Tor network is smoother.
- You can choose Entry Guard, Relay Nodes, and Exit Nodes.
Explaining TOR Nodes/Relays
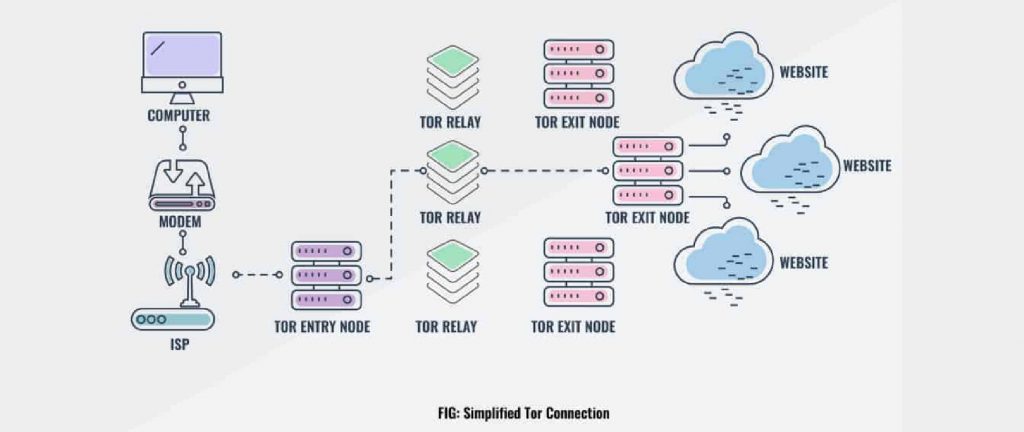
Nodes are also referred to as relays or routers. They are the most important part of the Tor network. These nodes help to anonymize the Tor connection and to maintain the Perfect Forward Secrecy. They receive all the traffic on the Tor network and pass it forward.
Each Tor connection consists of a minimum of three kinds of Nodes that we run to help the Tor network:
- Entry Node: This is the first node from which traffic enters the tor network. Relay nodes can be used as entry nodes as there is no such difference in their functions. Most information entry nodes can have been the user’s real identity and information of the following node. It does not know the user’s destination because of the Perfect Forward Secrecy.
- Relay Node: The relay nodes accept the tor connection. It peels off the additional layer of the Perfect Forward Secrecy to pass the connection to the next node to the forward path chain. The configuration has only one middle node; you can increase the number according to your choice but remember, if you increase the number of middle notes, the more the connection will be delayed.
- Exit Node: This Node is the final node communicating with the destination. When the Tor clients are connecting to any of the services (email providers, websites, etc.) can only see the exit relay instead of the real IP address of the Tor user. Exit nodes do not know your identity but know where you are going.
How is TOR Different from VPN
Tor and VPN proxy servers have specific features; they differ in some ways, but both are meant to protect your privacy. Here are some of the detailed differences between VPN and TOR.
VPN:
- Virtual Private Network (VPN) is not an entirely free app; you must go premium to access some features; some VPNs also come with a 30-day money-back guarantee.
- It is compatible with all devices.
- It is faster than the Tor.
- It can protect the user from all online connections.
- VPN routes your internet traffic through secure servers. It creates a secure and highly encrypted connection for the user, making it impossible for third parties to intercept or monitor their activities.
- It also helps to access geo-blocked content by changing your IP Address and shows that you are browsing from a different location.
- They are commonly used to protect your data on public Wi-fi networks to maintain privacy from your internet service provider.
TOR:
- The Onion Router (TOR) browser is free to download and use.
- Tor is not compatible with all the devices.
- It has a slower speed than VPN because of the onion routing and its encrypted layers of privacy.
- It cannot protect the user from all the connections.
- It routes the internet traffic through a series of volunteer-operated servers, which are encrypted at each step.
- The Onion browser provides you with high anonymity by masking your IP Address. It also makes your online activities difficult to trace back.
- TOR can access the dark web, which regular browsers cannot access.
Best Dark Web Search Engines
Search Engines are the most crucial part of web browsing. However, we have only discovered 10% of websites we have seen on the surface’s search engine. The remaining cannot be seen on the Google search engine.
Dark web websites cannot be listed on typical search engines. Search engines on the dark web are often called “onion web search engines” because conventional search engines like Google cannot access onion domains. Regular search engines cannot index the dark web.
Dark web search engines can help you browse dark websites and can be only accessed through IP Addresses, URLs, or deep/dark web search applications. Here are some of the top darknet browsers:
1. Ahmia
Despite being a surface web search engine, it is compatible with TOR’s onion services. Ahmia search engine can view statistics and news about Tor. Almost every other onion site is linked with illegal activities and malicious web pages, but Ahmia eliminates fake and unsafe websites that can contain Malware.
Haystack
Haystack is a dark web search engine with over 1.5 billion indexed pages. It protects your privacy and does not track your data. The free version of Haystack will show you ads. Therefore, you have to spend some money to switch to the premium version to lose the ads and get access to historical versions of websites.
2. Hidden Wiki
Hidden Wiki is not a search engine for the dark web; however, it makes Tor easier to use by providing a categorized index of Onion websites and surface web links. It also uses filters to block scams and malware sites like other search engines and does not block some shady websites that Google blocks.
3. DuckDuckgo
DuckDuckgo (DDG) is considered Google for the Dark Web. It has a search box in the middle, and its search result list is like Google. It is one of the best private search engines. They have a no-log policy and cannot track your search history or gather information. DuckDuckgo is a deep/dark search engine that works for surface websites.
4. Torch
Torch is a popular and one of the oldest dark web search engines. It indexes a large number of onion sites on the Tor network, and loads comparatively fast. It is considered the best search engine for exploring the dark web.
One disadvantage of Torch is its inability to filter out dangerous websites that are popped up on all the dark web search engines. You might open malicious or harmful while using the Torch search engines.
5. Not Evil
Not Evil is also a search engine for the dark web, and its name is a play on Google’s motto, “Don’t be evil.” It indexes over 32 million websites and more than 14 million onion links from Tor Servers. The search results rely on a community of volunteers who can report misleading results and can report as abusive.
It actively tries to fight against searches like “child pornography,” which is safe to show and promote legal activities on the dark web. The only annoying thing about this search engine is Not Evil servers are usually down.
6. Candle
The Candle is a dark web search engine popular among Cybercriminals to buy illegal things from the dark web market. It has 100,000 web pages, including dark web marketplaces. It is effective but minimal, only shows you the most relevant top ten search results, and cannot read characters like quotation marks, etc.
7. Kilos
Kilo, this search engine, is used to access the darkweb markets. As the name suggests, it is a big marketplace for selling and purchasing illegal drugs. As it does not filter search results, it has become one of the premier search engines for accessing the black market; it is a dangerous entryway filled with potential threats.
8. Dark Search
It is a comparatively new search engine for the dark web. Also, it aims to give users free access to visit onion links and sites.
How Did the Dark Web Come into Existence

The Dark Web was developed in the late 90s by two research organizations in the US Department of Defense as an encrypted network and unnamed source for US spies so that they can communicate sensitive information.
The idea was that ordinary surfers on the Internet could not access this kind of network. It requires a special web browser like Tor and VPN to access it. Its content and material are hidden from search engines, so it can’t be found easily and will allow users to conceal their identity completely as they don’t have greater search engines like the surface web; the user must find the onion websites, and the addresses are very hard for one to remember many organizations are part of Dark web and have access to them.
Big organizations like the CIA, BBC, and Wikileaks are users of the Dark Web. Some people around the world use the Dark web for all the right reasons, like if they want to talk about something but their country has strict laws about censorship, the government of that country also uses it.
Whereas Dark Web these days is only used for illegal activities, crimes and inhumane things have been normalized on this deeper level of the Internet.
Reported Crimes That are Common on Dark Web
It is important to note that accessing the dark web search engines involves navigating through layers of anonymity and encryption. The dark web might be legal, but at the same time is a platform for horrible crimes and other illegal activities.
Things commonly reported on the Dark Web are; People here can buy and sell stolen identities that can be misused while attempting horrible crimes and other illegal activities. Criminals offer counterfeit money on the Dark Web, weakening the financial system and causing economic harm. Also, you can hire a professional killer to kill someone or to watch a child being sexually abused, being molested, or being tortured. The dark web is as dark as its name.
Here we mention some ill-repute and notorious cases of the darkweb.
1. The Demand for Steakandcheese
Rotten and Steakandcheese are websites where people can watch gruesome horrendous violent videos of people shedding blood. It is sad to know that these videos are still growing and are gaining popularity, showing how dark and twisted these websites and their users can be.
Surprisingly in the early 2000s, Google indexed the Steakandcheese website, showing Gorey (bloodstained) videos. However, now Google does not index this website on the surface web.
1. The Monstrous Case of Peter Scully
An Australian man named Peter Scully is serving a life sentence in the Philippines after being found guilty of committing sickening crimes like human trafficking and sexually abusing minors. He also was on trial for spreading child pornography, torturing and murdering them. He used to record everything mentioned above to upload them on the Dark web.
2. Arrest of Hieu Minh Ngo
Hieu Minh Ngo is known for being an international criminal and a mastermind behind massive wire frauds, device frauds, and stolen identities. He made almost $2 million.
But in 2013, he was tricked into coming to the US for a huge business deal and was promised that he would be given some financial and personal data to sell on the dark web. Unfortunately, when he reached the US, there was no business deal; the “partner” waiting for him was an undercover agent of the US Secret Service. Hieu Minh was then arrested and sentenced to 13 years of imprisonment.
3. The Silk Road Black Market
The man behind the infamous black market was Ross Ulbricht, aka Dread Pirate Roberts, who did earn around $3.6 million. The platform was a market like eBay and Amazon for merchants to sell their illegal products users were a few clicks away from buying those explicit content, drugs, and even guns. In 2013 he was arrested and is serving a double life sentence.
4. RockYou2021 Password leak
A file of 100 GB with around 8.4 billion passwords of users was uploaded on anonymous hackers’ profiles for sale. No doubt, cybercriminals spend a lot of time hacking passwords for various inappropriate reasons through data breaches or ransom attacks.
5. Crimes of Shannon McCoole
Shannon McCoole is one of the sick Dark web criminals; he used to sell sexually explicit content, molesting, and torturing children. Not only that, but he ran the largest child pornographic website on the dark web. Furthermore, being a pedophile himself, he sexually abused multiple children over three years since 2011. He was finally arrested in 2014 for sexually abusing young children around 18 months.
FAQ
Selling illegal drugs, counterfeit currency, identity theft, pornography, etc.
No, many other big organizations like BBC, CIA, WikiLeaks, and ProPublica use the dark web. Journalists also use it to publish clandestine work.
Fortunately, you cannot access the dark web on a regular browser. You have to download the Tor browser, and thanks to the Onion Routing, it keeps your online activity encrypted; hence your ISP won’t know that you are accessing the dark web.
No, Incognito mode won’t save your history or cookies when you access the dark web; however, it still can see your IP Address; it is better to use Tor to enhance and save your privacy and security when exploring such a dangerous and harmful platform.
Data Breaches and Malware are the two common ways your personal information can end up on the dark web. Data Breaches mean that your personal information will be stolen and sold on the dark web, whereas Malware can harm your computer and can send fake emails from your account.
Yes, there might be a chance that your data or personal information is leaked or stolen, and it might be somewhere on illegal websites or blogs living on the dark web; you might never know. However, you can always take precautions before browsing the Internet and avoid clicking on links that keep popping up on websites.
No matter where you live, several times you might have encountered restricted links and blocked sites; your government could have blocked these areas of the Internet to suit their agenda. However, there are different ways to access them; one of the easiest ways is to use VPN (Virtual Private Network).
Conclusion
We have entered a world where everything is changing every day. The Internet is no longer the same as when it became publicly accessible in the 1990s. It has become more complex as it comes with three layers Surface web, Deep web, and Dark web.
The Dark web is the deepest and most concealed portion of the Internet; it can’t be accessed without a specific browser; the best known is The Onion Router. More than 2 million people use Tor as it helps to conceal and protect your real identity by masking your original IP Address while you are exploring onion sites.
The dark web has not got a good reputation. As it is now widely known for its illegal activities, including cybercrimes and identity theft, you can stumble upon scams and threatening sites while browsing the dark web, and your personal information can end up on sites handled by criminals and hackers.
So, one must be careful and know all the cons of surfacing on the dark web to keep your private life off such sites. While browsing the dark web, the user must guard their privacy by enhancing their TORs browser security by using VPN. Nonetheless, Tor plans to develop a VPN-like software by collaborating with Guardian Project, known for proxy servers and Orbot, to enhance their security.

